🚀 Introduction: The Key to Trust in a Trustless System
Imagine you want to send a locked box 📦 to a friend, Bob, but you don’t want anyone else to open it. Bob has a special lock 🏆 that only he can unlock with his private key, while anyone can lock it with his public key. That’s the essence of asymmetric cryptography!
Bitcoin uses this principle to protect transactions, ensuring that only the owner of a private key can spend their Bitcoin, while everyone can verify ownership using the public key. But how does this actually work? Let’s dive in!
🔑 Core Explanation: How It Works
Asymmetric cryptography (also known as public-key cryptography) relies on a pair of cryptographic keys:
- ✅ Public Key (🔓) – Shared with everyone. Used for encrypting data and verifying signatures.
- 🔒 Private Key (🔑) – Kept secret. Used for decrypting data and signing transactions.
Step-by-Step Breakdown 📝
- 1️⃣ Key Generation: A user generates a private key (a long random number). From this, a public key is mathematically derived.
- 2️⃣ Encryption: Anyone can encrypt a message using the recipient’s public key, but only the recipient’s private key can decrypt it.
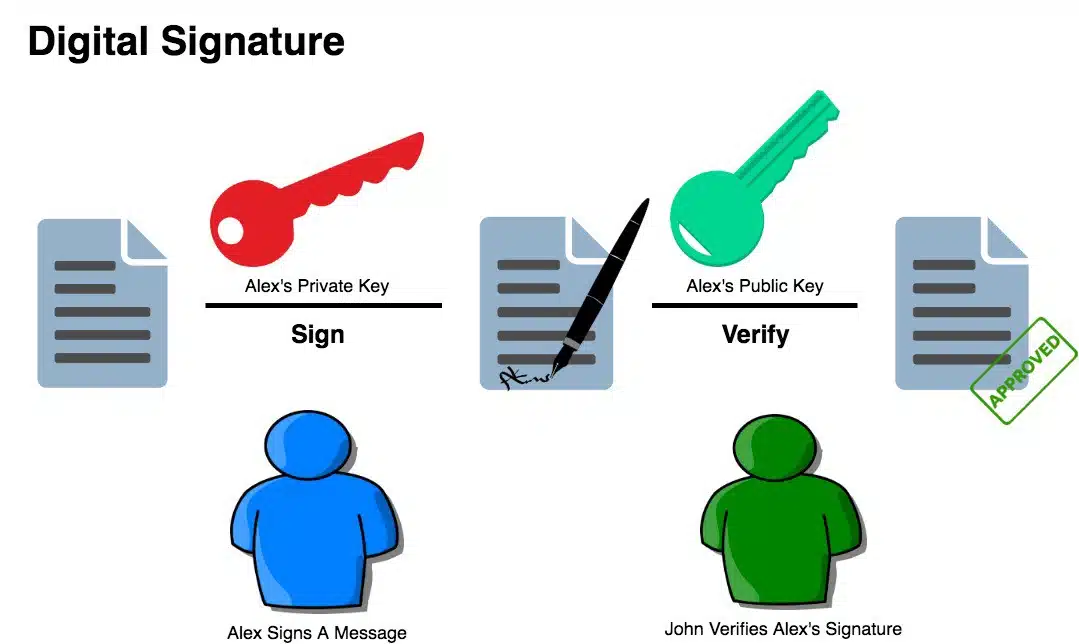
- 3️⃣ Digital Signatures: When sending Bitcoin, the sender signs a transaction with their private key, proving ownership.
- 4️⃣ Verification: Others can verify the signature using the sender’s public key without revealing the private key itself.
Bitcoin transactions rely on Elliptic Curve Cryptography (ECC), which is an efficient method for generating public-private key pairs.
🎨 Visual Breakdown
Here’s a simplified diagram of how asymmetric encryption works:
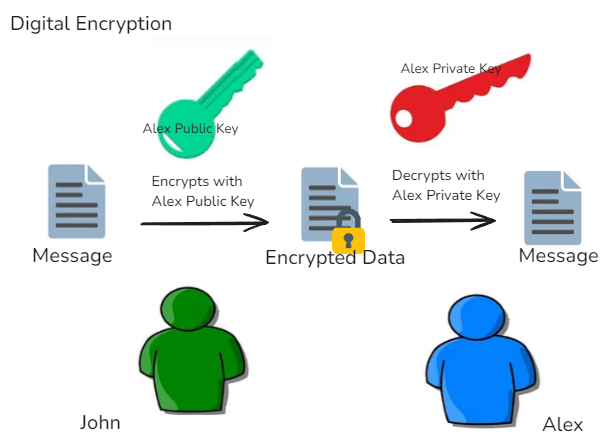 And here’s how digital signatures work:
And here’s how digital signatures work:
Once already we understood that we can image nodes to be verifying the users signatures to prove their funds:
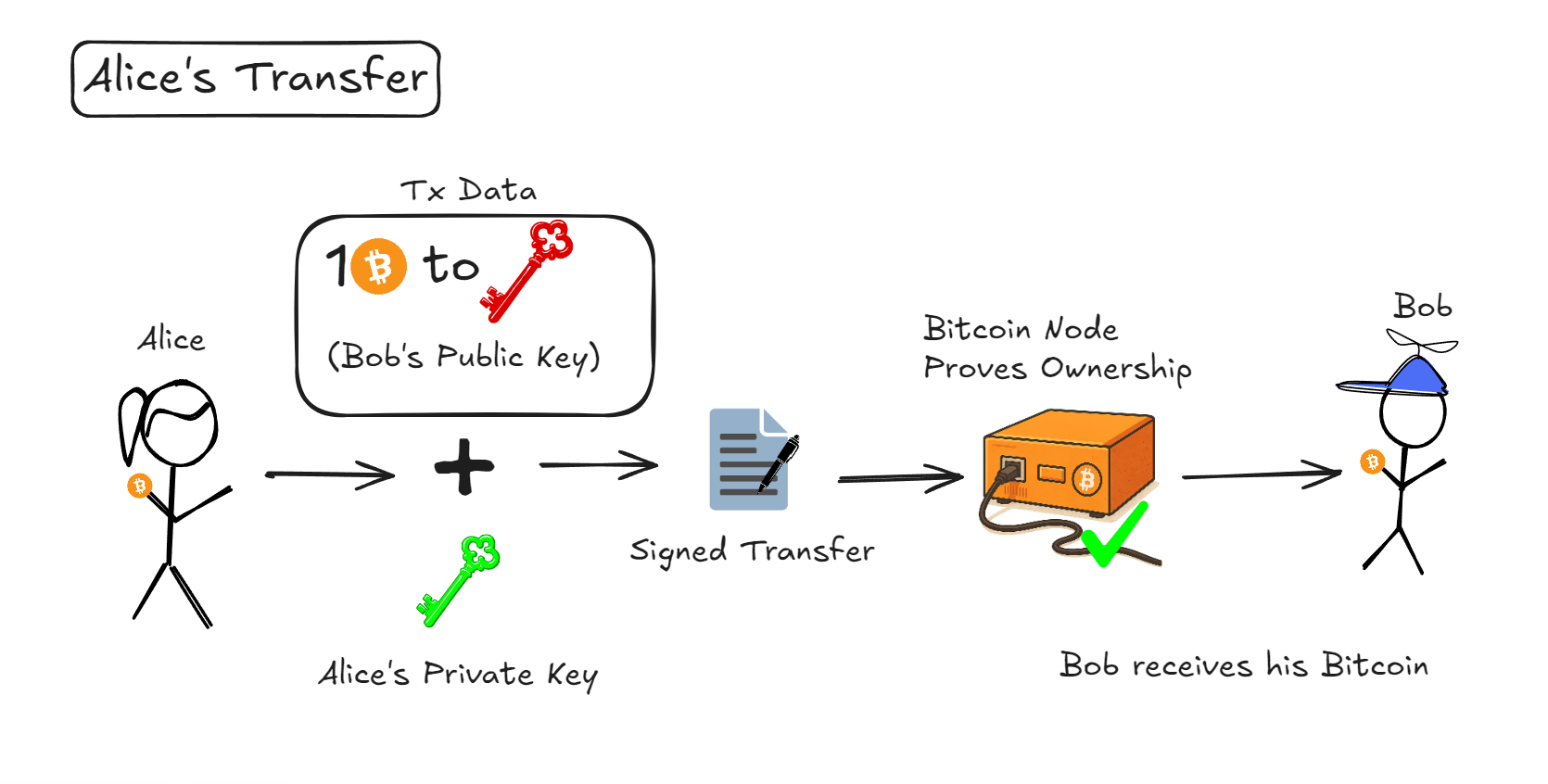
🏦 Real-World Example: Alice Pays Bob
Let’s say Alice wants to send Bitcoin to Bob. Here’s how asymmetric cryptography secures the process:
1️⃣ Alice creates a transaction:
- She specifies Bob’s public key as the recipient.
- She signs the transaction with her private key.
2️⃣ The network verifies:
- Nodes use Alice’s public key to check if the signature is valid.
- If the signature is correct, the transaction is confirmed.
3️⃣ Bob receives Bitcoin:
- Since only Bob has his private key, he is the only one who can unlock and spend the funds.
🛡️ Security & Importance
Why Asymmetric Cryptography Matters in Bitcoin
✅ Prevents Theft: Without the private key, no one can access your Bitcoin.
✅ Verifiable Transactions: Anyone can verify a transaction’s legitimacy without exposing sensitive data.
✅ Decentralization: No need for a trusted third party—math ensures security.
🔥 Potential Threats
⚠️ Private Key Theft – If someone gets your private key, they can steal your Bitcoin. (Solution: Use cold wallets and strong security practices!)
⚠️ Quantum Computing – Future quantum computers might break current encryption. (Solution: Research into quantum-resistant cryptography is ongoing.)
🎯 Final Thoughts
Asymmetric cryptography is what makes Bitcoin trustless yet secure—you don’t need to trust anyone, just the math behind it! 🧮💡
